Cryptocurrencies are the hot trending topic and have the tremendous potential to affect almost every sector. It has managed to attract the attention of governments and other agencies as the market cap of cryptocurrency has already crossed $284 billion. Cryptocurrency is the digital assets and optimizes the concept of cryptographic protocols for encryption of the events such as transactions and data exchange. Additionally, it is based on decentralized and distributive structure, thus negates the concept of any central authority.
Cryptocurrency is disrupting the conventional market by removing the intermediaries such as banks and financial institutions that have the capability to cause inflation by producing the physical currency. On the other hand, Cryptocurrency is generated through the process of mining which involves the process of solving the mathematical equations by the miners and in return, they get rewarded with some coins.
Exploring Anatomy of a Transaction in Cryptocurrency Exchanges
The elements involved in the whole process of transaction is
– An Input (public address of Alice)
– The amount to transact
– An Output (private address of Bob)
Now suppose, Alice wants to purchase grocery from the online shop of Bob, and the total cost involved in the transaction is USD $20. Let’s say, the current exchange rate is 0.000086BTC to 1 USD. Then, the total amount to be paid by Alice is 0.00172 BTC. The moment this transaction will take place it will get broadcasted into the peer to peer network.
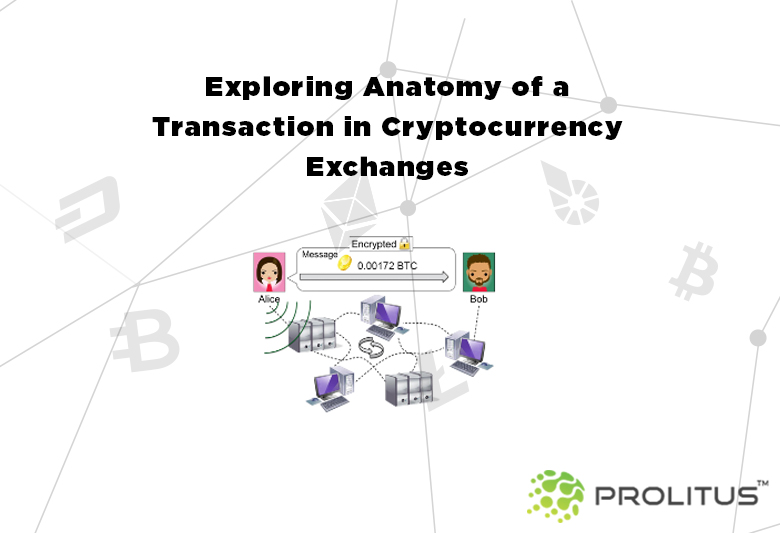
The use of public and private keys is made for encrypting and decrypting the information respectively. Earlier the prevalent method for cryptography was symmetric key cryptography, which suffered from the secure-key-exchange problem. Under symmetric key cryptography same key was used in the phase of encryption and decryption that posed a threat- what if someone gets hold of that key?
Asymmetric key cryptography overcame this problem by making use of two separate keys i.e. public and private for the purpose of encryption and decryption. For example, suppose A wishes to send some message to B, then A will encrypt the message using B’s Public Key (available to everyone) and send it. Now, B will have a Private Key (available only to B and hidden from the others) to decrypt the message. Its in-depth working can be understood by understanding the RSA algorithm. The RSA public-private key encryption algorithm involves the following steps:
- Key generation i.e. Public and Private keys
- encryption of the plaintext(message) using the private key to get the cipher-text.
- Decryption of the cipher-text using the corresponding private key.
Also Read: How To Keep Your Cryptocurrency Safe?
Hash Function: A Hash function ensures that the values have not been changed or tinkered with. A one -way hash function takes the input (that can include a set of string, pdf file, video and email etc.) and produces a fixed length of output.
Any attempt to change the information – even by just one bit- will change the output value entirely. And also, it is not possible or feasible to reconstruct the original input or message from the hashed output value.
The Proof-of-Work system: It is a method of reducing spams and eliminating the possibility of service attacks by making a computer put some processing power and time to solve something. Hashcash is one such proof-of-work algorithm that is used in crypto-currencies. It requires a proof that the person who has sent the email has spent a certain amount of time and computational power to solve some puzzle and it is unlikely that the sender is a spammer as it won’t be profitable for the spammers because of the requirement of some cost, for each spam.
How does Peer-to-Peer Network work?
In a peer-to-peer network, a message is broadcasted across the network by the nodes that Alice is transferring some currency to Bob. Each node keeps the complete detail (including history) of ledger transactions. And it is done to assure that Alice indeed has 0.00172 BTC.
Some other functions of a node are:
– Keeping the public ledger
– Verification of transactions
– Updation of the ledger upon creation of new ledger pages
– A node also can mine and add new blocks (optionally)
The Process of Mining
The mining process has been intentionally designed to be difficult and resource-intensive in order to keep the number of discovered blocks steady. And the main motive behind mining is to bring all the nodes to a secure and tamper-proof consensus level.
Every cryptocurrency chooses an apt algorithm for getting its coins mined. SHA-256 and Scrypt algorithms are most commonly used for mining purpose.
SHA-256: It is the first algorithm to be used with a cryptocurrency i.e. Bitcoin. SHA-256 stands for Secure Hash Algorithm. It is used by miners for confirming the transactions and maintaining the network via proof of work.
Scrypt: The Scrypt algorithm is a proof-of-work algorithm. Litecoin uses this algorithm as it is considered a fast and relatively simple algorithm for calculating blocks or hashing.
The mining process of every block takes approximately 10 minutes of time (for Bitcoin). It involves a phase of solving the puzzle which is similar to guessing a number on a combination lock. And brute force is the only option to solve the puzzle, there is no any other smart work. The process involves some effort for earning the reward and this is the reason it has been termed as ‘mining’.
When a block is discovered after agreed-upon by everyone, the miner is rewarded with a certain number of coins.
Factors defining the price of cryptocurrency
A few factors that act as the driver of cryptocurrency price are:
- Bitcoin Value: Since the rise and fall of Bitcoin impact the value of other cryptocurrencies.
- Number of Investors: Presence of a large number of investors enhances the confidence in other people and increases the demand or price of cryptocurrency.
- Scams: Incident of scams affects the value of cryptocurrency. For example, when the developers dump their pre-mined holdings or coins, it crashes the value for other investors.
- Public Perception: Public perception of a cryptocurrency, positive or negative, matters a lot when it comes to the value of the currency.
- Demand and Supply: Theory of demand and supply is the basic factor that affects the price of cryptocurrency.
Prolitus Technologies has developed Native Cryptocurrencies for clients from different industries and possess the experience and the right competence to address the requirements of varied business processes. To know more about Cryptocurrency Development services offered by Prolitus, drop an email at success@prolitus.com






